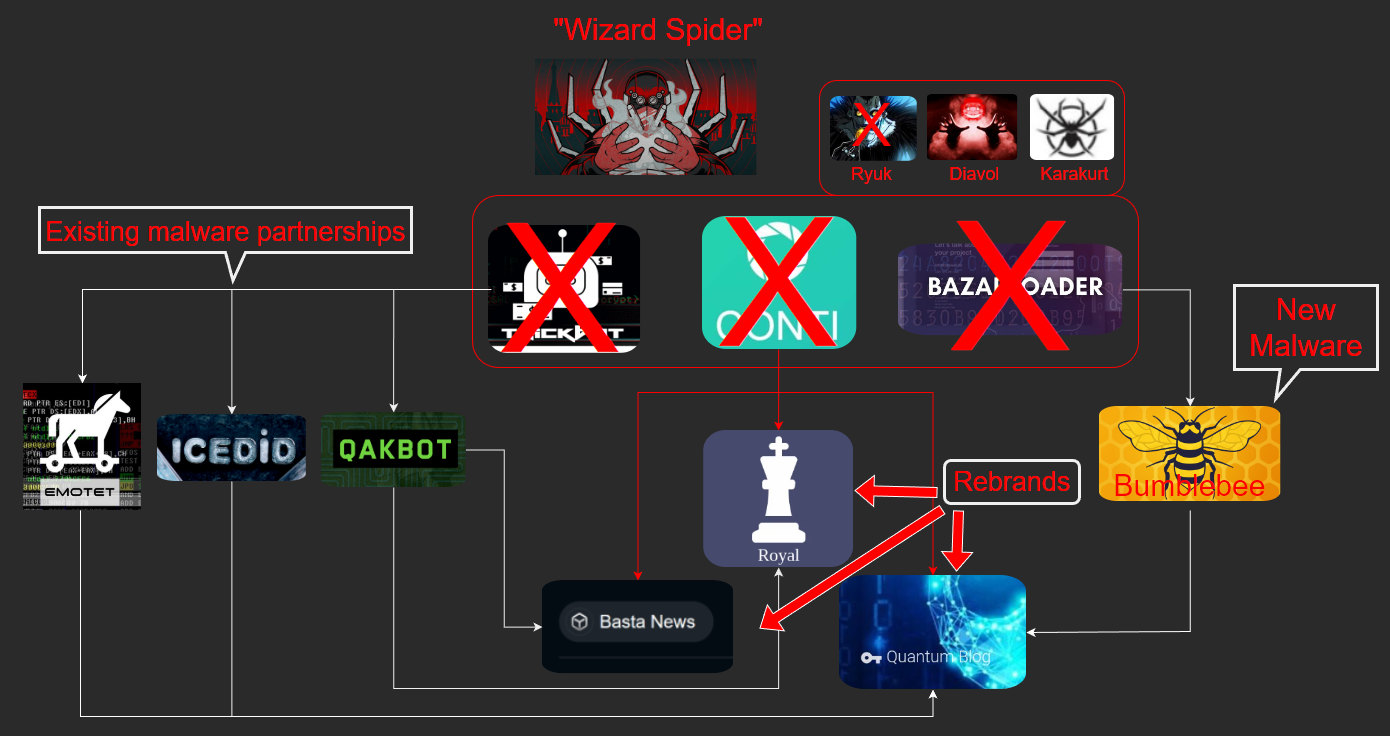
The Continuity of Conti
In February 2022, following the Russian invasion of Ukraine, the operators of Conti ransomware announced their support of the Russian government. They shortly walked back their support, seemingly after rifts by members of the group. Not long after that, hundreds of thousands of messages from internal chat logs were shared publicly by two accounts on Twitter called @ContiLeaks and @TrickLeaks. This treasure trove of information revealed a wealth of insights about the inner workings of a sophisticated Russian cybercrime business linked to the Conti and Ryuk ransomware campaigns and Trickbot malware botnet, which are tracked as Wizard Spider (by CrowdStrike), DEV-0193 (by Microsoft), GOLD ULRICK (by Secureworks), and Ryuk as FIN12 (by Mandiant).
Following the fallout of the internal chat leaks, the Conti ransomware group carried on, seemingly business as usual. In April 2022, the Government of Costa Rica had to declare a state of emergency following a sprawling Conti ransomware attack. After this incident, however, Conti seemingly slipped away into the shadows, shut down their leak site and stopped using the ransomware in attacks. The group's BazarLoader malware and Trickbot malware families had also ceased to spread in the wild. It seemed Conti had shut up shop and moved on, cutting their losses and perhaps contemplated leaving cybercrime behind.
Unfortunately, they didn't. The members of Conti have continued attacks, but seemingly under several different names, including Quantum, Royal, and Black Basta (also highlighted by Vitali Kremez here). Campaigns previously attributed to Conti such as Karakurt and Diavol have also continued in 2022 since the leaks. These new data-theft-extortion ransomware campaigns, though, have been supported by malware other than Trickbot and BazarLoader, this includes the new BumbleBee malware, as well as three malware botnets previously associated with Conti attacks: IcedID, Qakbot, and Emotet.
The ties between Conti, Quantum, and BumbleBee campaigns are strong and have been publicly documented by several vendors and multiple research teams. The ties between Conti, Royal, and Black Basta ransomware, however, require bit more inspection and research.
Conti & Quantum
In March 2022, shortly after the internal chat leaks, a new malware family dubbed BumbleBee (named after a user-agent string in the malware) appeared and was connected to the BazarLoader and IcedID by Proofpoint analysts. The malware was also associated with an initial access broker (IAB) tracked as EXOTIC LILY by Google TAG whose attacks reportedly led to the deployment of Conti or Quantum ransomware. Kroll researchers provided further connections to Conti by sharing BumbleBee C2 servers used prior as Ryuk and Conti shared infrastructure, as well as the IcedID malware, which has also been used in Quantum Locker ransomware operations. Microsoft tracks the ransomware activity group that shifted from Conti to Quantum as DEV-0230, who are "one of the most prolific and successful Conti affiliates". Interestingly, DEV-0230 also deployed FiveHands and HelloKitty via BazarLoader infrastructure.
Conti & Black Basta
Security researchers from Palo Alto Networks Unit42 highlighted that "based on multiple similarities in tactics, techniques and procedures (TTPs), victim-shaming blogs, recovery portals, negotiation tactics, and how quickly Black Basta amassed its victims, that the Black Basta group could include current or former members of the Conti group." Microsoft's Cyber Signals report from August 2022 also stated that DEV-0390 is "a former Conti affiliate who deploys penetration testing tools like Cobalt Strike, Brute Ratel C4, and the legitimate Atera remote management utility to maintain access to a victim." Microsoft also shared that another activity group tracked as DEV-0506 was "deploying BlackBasta part-time before the Conti shutdown and is now deploying it regularly." In October 2022, Trend Micro shared another potential overlap between Conti and Black Basta after reporting that operators do use Cobalt Strike and Brute Ratel C4 in attacks, which also begin with a Qakbot infection.
Conti & Royal
Royal ransomware became public knowledge in September 2022. The late Vitali Kremez, told BleepingComputer that Royal ransomware attacks utilized callback phishing. Although these callback phishing attacks did not lead to the BazarLoader, the tactic was certainly popularized by the Conti group's associates and was dubbed the BazarCall campaign. Other minor links to Conti include that the ransom note of Royal ransomware is nearly identical to Conti's and uses "RestartMgrSvc" boilerplate code to free up locked files via "Rstrtmgr.dll". The Royal ransomware campaign is currently separate from Black Basta and Quantum. In November 2022, Microsoft shared that it tracks this activity group as DEV-0569 and found that the BATLOADER malware family was leading to Royal ransomware deployment. BATLOADER uses SEO poisoning to pose as installers or updates for legitimate applications like Microsoft Teams or Zoom. Once inside the victim's network, BATLOADER has led to other malware families, such as Ursnif Gozi, Vidar Stealer, and Cobalt Strike Beacons, as well as the legitimate Synchro remote monitoring and management (RMM) tool.
Remnants of Conti
Security researchers have also highlighted recently compiled versions of malware associated with Conti and WizardSpider several months since the internal chat leaks and shutdown of the Conti News darknet leak site.
In April 2022, Google TAG identified multiple email phishing campaigns delivering malware associated with WizardSpider. This activity is tracked as UAC-0098 by CERT-UA. Possibly most interestingly it "rather uniquely" demonstrated a "strong interest in the hospitality industry of Ukraine, going as far as launching multiple distinct campaigns against the same hotel chains".
In July 2022, IBM X-Force also reported that there had been an "unprecedented shift" by members of Trickbot, Conti, and WizardSpider to target Ukrainian organizations. The group conducted six campaigns between April-June 2022, during which they deployed IcedID, CobaltStrike, AnchorMail, and Meterpreter.
In September 2022, Walmart Global Tech observed newly created versions and variants of the Diavol ransomware uploaded to VirusTotal. The Diavol ransomware samples are now 64-bit but function similarly.
These three developments highlight how different aspects of the WizardSpider operation continue to remain active separate from each other. These interconnected and parallel operations with widely varying objectives dismantle the idea that there is one organized threat group behind it all.
Key Takeaways
- There are several substantial links between Quantum, Black Basta, and Royal ransomware families to Conti ransomware campaigns, these activity groups are currently the most likely successors of the Conti group
- Tracking WizardSpider as a monolithic threat group is an unrealistic view of how this sprawling cybercriminal ecosystem operates and does not account for developers, operators, or affiliates who are connected to multiple ransomware groups
- The Conti leaks further highlighted that sophisticated Russian cybercrime businesses can continue to operate despite major disruptions, albeit in separate clusters and splinter groups
- A multi-million-dollar industry has formed around the ransomware ecosystem and the major players continue to participate and extort large corporations, despite major disruptions such as leaks, arrests, sanctions, or asset seizures