
The Lapsus$ data extortion group leaked today a huge collection of confidential data they claim to be from Samsung Electronics, the South Korean giant consumer electronics company.
The leak comes less than a week after Lapsus$ released a 20GB document archive from 1TB of data stolen from Nvidia GPU designer.
Gang teases Samsung data leak
In a note posted earlier today, the extortion gang teased about releasing Samsung data with a snapshot of C/C++ directives in Samsung software.
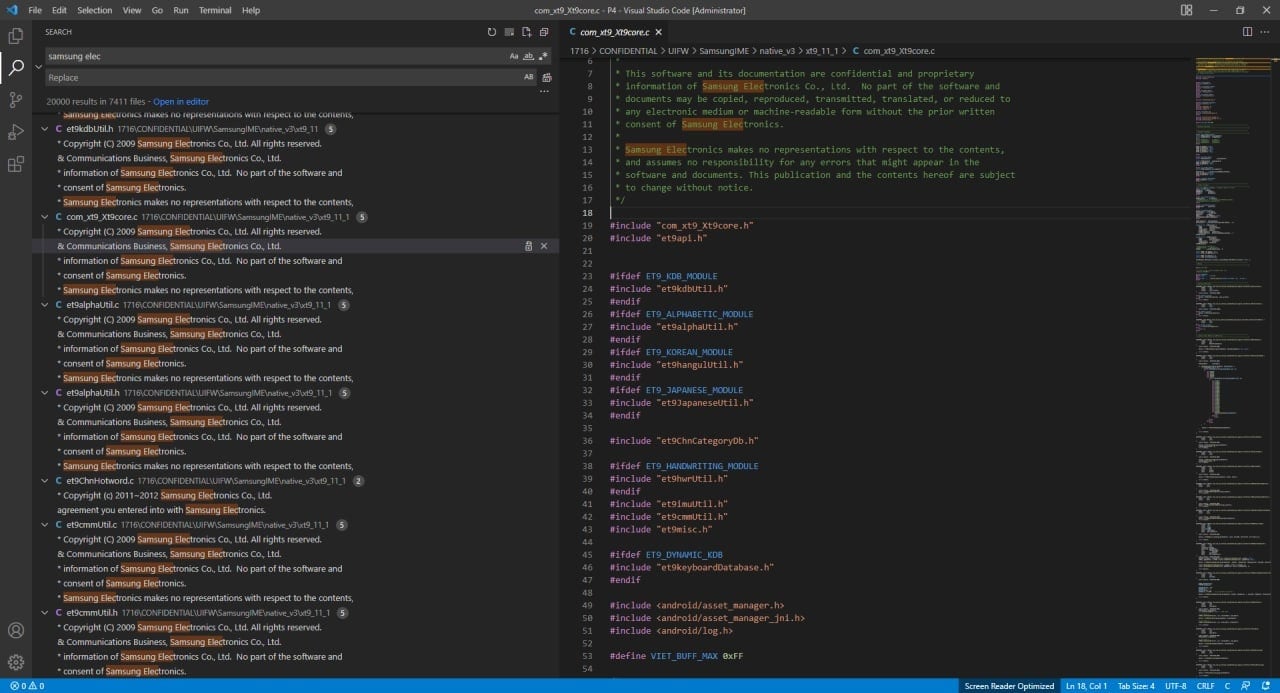
Shortly after teasing their followers, Lapsus$ published a description of the upcoming leak, saying that it contains “confidential Samsung source code” originating from a breach.
- source code for every Trusted Applet (TA) installed in Samsung’s TrustZone environment used for sensitive operations (e.g. hardware cryptography, binary encryption, access control)
- algorithms for all biometric unlock operations
- bootloader source code for all recent Samsung devices
- confidential source code from Qualcomm
- source code for Samsung’s activation servers
- full source code for technology used for authorizing and authenticating Samsung accounts, including APIs and services
If the details above are accurate, Samsung has suffered a major data breach that could cause huge damage to the company.
Lapsus$ split the leaked data in three compressed files that add to almost 190GB and made them available in a torrent that appears to be highly popular, with more than 400 peers sharing the content. The extortion group also said that it would deploy more servers to increase the download speed.
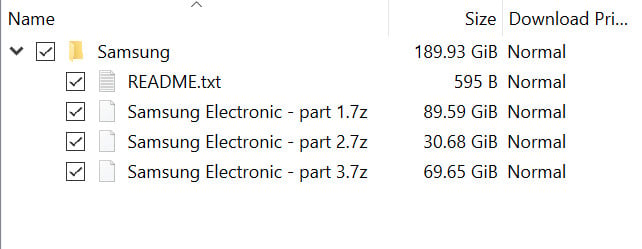
Included in the torrent is also a brief description for the content available in each of the three archives:
- Part 1 contains a dump of source code and related data about Security/Defense/Knox/Bootloader/TrustedApps and various other items
- Part 2 contains a dump of source code and related data about device security and encryption
- Part 3 contains various repositories from Samsung Github: mobile defense engineering, Samsung account backend, Samsung pass backend/frontend, and SES (Bixby, Smartthings, store)
It is unclear if Lapsus$ contacted Samsung for a ransom, as they claimed in the case of Nvidia.
BleepingComputer has contacted Samsung for a statement about the Lapsus$ data leak and will update the article when the company replies.
Update [March 7, 2022]: Samsung confirmed a data breach on its systems and that the intruder had access to source code used in Galaxy smartphones.


Comments
Ryan223 - 2 years ago
Thank you for this important story. Very surprised there hasn't been any follow-up stories from other outlets or statements from Samsung since this could potentially expose several 100 million phones to attack
Can you submit a press inquiry to Samsung to make a statement on the massive leak of security files, encryption and security protocols released to the public a few days ago by the Nvidia hackers?
Will this mean all our Samsung phones are vulnerable to backdoor hacks and other hijacking of keyboard loggers/camera/mic?
Could this info be used by hackers to brick millions of Samsung phones?
Is it fixable with security updates?
Is it now unsafe to use online banking or input other sensitive passwords or info into our phones?
Are saved passwords and accounts in Samsung phones now vulnerable?
Just got a new $800 Galaxy S22 but now afraid to use it. Hope Samsung will make at least some initial assessment of the danger to end users soon beyond "We're assessing the situation". Not even a whisper of it on Samsung's website. Hopefully that doesn't mean they are going to ignore it...
ilaion - 2 years ago
We asked Samsung to comment about the leak and to answer a few questions and are waiting for a reply.