Key Takeaways:
- Personal health information (PHI) is an incredibly valuable category of personal data. When compromised and sold on the dark web, this data can be sold for thousands of dollars.
- Healthcare is a valuable target to attackers, including the group Killnet, which targeted healthcare sites in January 2023 with attacks that totaled over 6 times the average requests per second (RPS).
- Shadow APIs pose a small, but significant, threat to the industry.
- Good bots can provide helpful information to those who need care, but bad bots, at 32% of all traffic, are responsible for a multitude of attacks that aim to gather PHI and disrupt important digital healthcare services.
- Account takeover is a significant risk for the healthcare industry, given the wealth of data stored in patient portals.
Background
The healthcare industry is a lucrative target for attackers, and accounts for about 6% of attacks that Imperva tracks across all industries.
Modern healthcare is reliant on many helpful digital services and technologies that create and store patient data. In an effort to make electronic health records shareable among healthcare and insurance providers, the United States’ 21st Century Cures Act, signed into law in 2016, made APIs imperative for the healthcare industry’s future. Electronic health records allow protected health information to be shared quickly and easily among providers and allow for continued care.
Unfortunately, PHI is one of the most valuable forms of data on the dark web. Because PHI is enduring – unlike a stolen credit card number that can be disabled – and comprehensive, it can be worth 1000 times the average price of data, compared to a card number or social security number (SSN). In addition to the resale value of PHI, attackers believe that healthcare services are more likely to pay ransom if patient services or medical functions are affected. In fact, the healthcare industry pays the highest volume of ransom payments per year, and the FBI listed healthcare as the leading industry targeted by ransomware attacks in 2021. Disruptions caused by a cybersecurity incident can jeopardize human lives by interrupting life-saving digital services. Some organizations may even prefer paying the attacker’s ransom rather than investigating or mitigating an attack because the priority is making systems operational to ensure continuity of care.
DDoS
DDoS attacks on healthcare providers’ systems can be life-threatening. If systems are down, it disrupts medical professionals from providing treatment or triaging urgent care. Therefore, rather than taking the time to mitigate the attack and bring systems back online, it can be tempting to pay the attacker’s ransom in hopes of returning to an operational state.
In the past 12 months, network DDoS attacks on healthcare sites have experienced a rollercoaster of activity. Large attacks on specific providers occurred every few months, which, if unprotected, would result in massive downtime and remediation efforts.
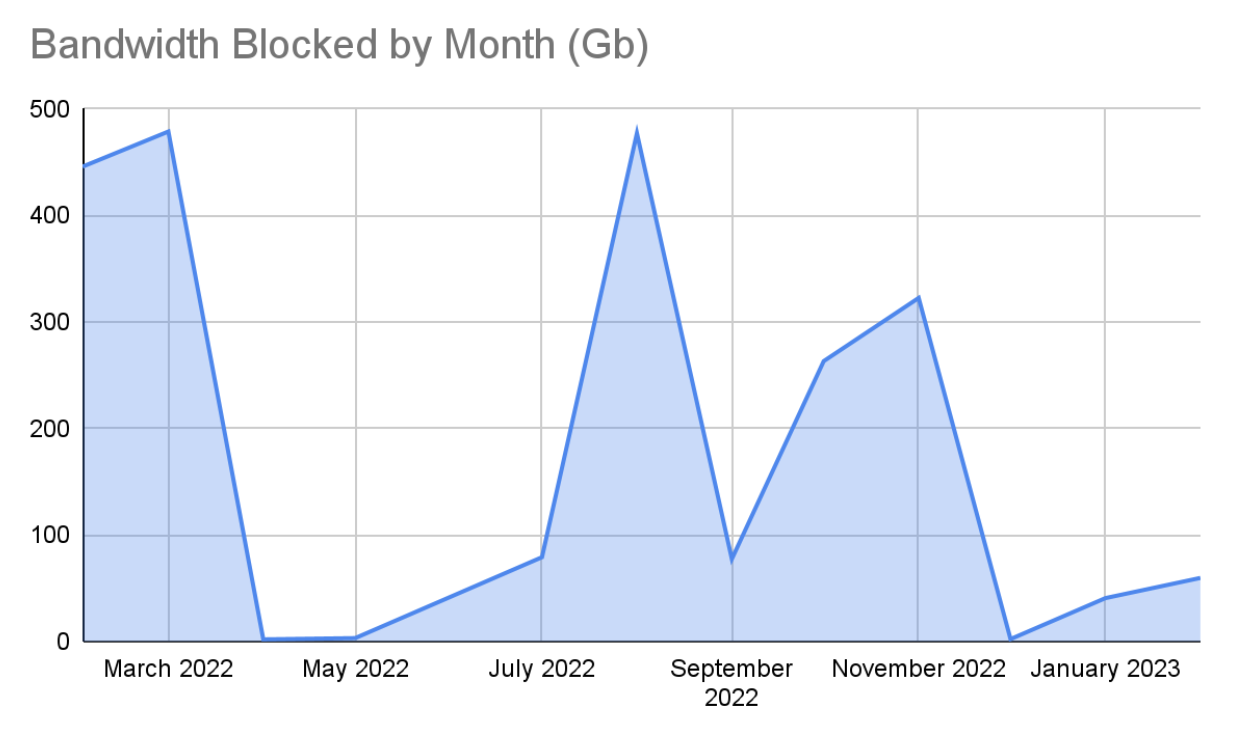
Killnet
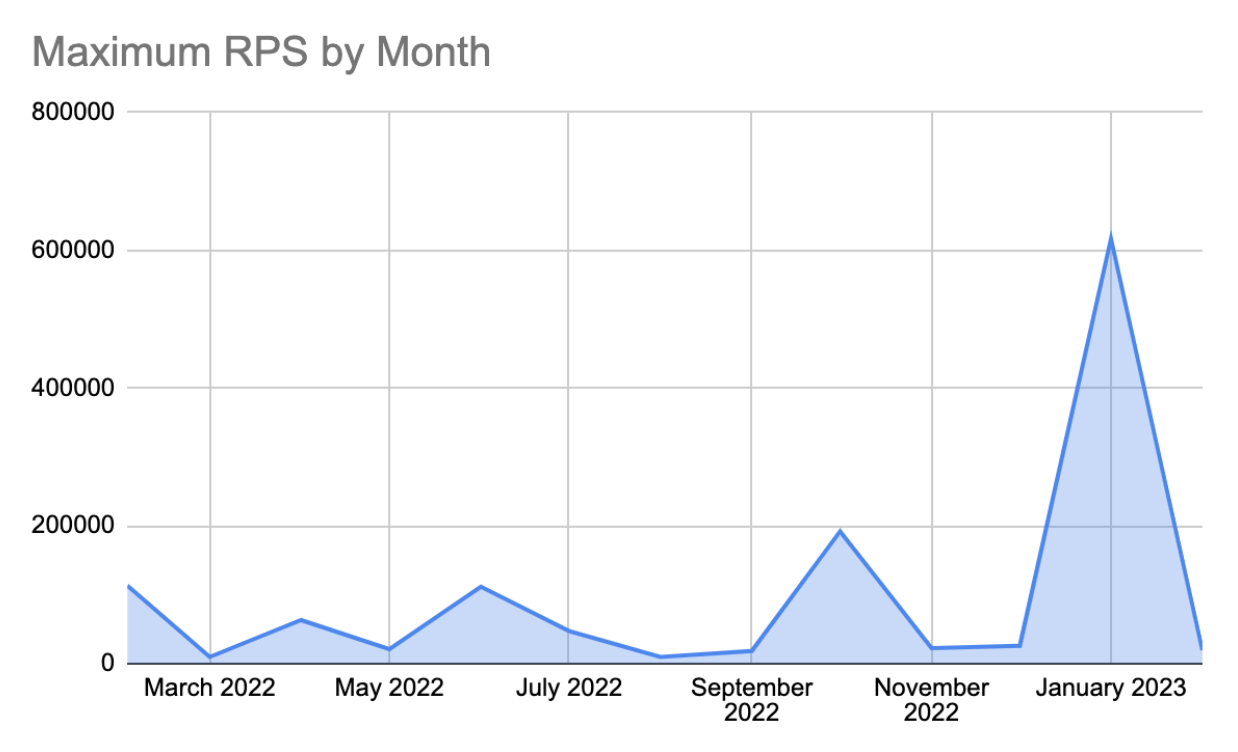
Killnet, a Russia-supporting DDoS collective, recently published a list of US healthcare targets, of which Imperva has tracked attacks on some of the sites. Within two days, over 9500 IPs targeted these sites, 66% of which used proxy servers.
Killnet aims to use DDoS to support its ideological goals, and they know that healthcare services are a ripe target. Application DDoS attacks targeting healthcare sites spiked in January because of Killnet’s activity. After publishing the target list, attacks spiked over 600,000 RPS on January 31.
Web Application & API Protection (WAAP)
Protecting APIs and other vulnerabilities in web applications is crucial for mitigating malicious attacks on the healthcare industry. For example, APIs are now used extensively in electronic health record (EHR) systems to share important information with patients and other providers, such as health insurance information and lab results. For attackers, APIs with inadequate protection are a rich target because they’re a pathway to a treasure trove of medical and financial data.
In the last year, remote code execution was the leading known attack against healthcare targets.
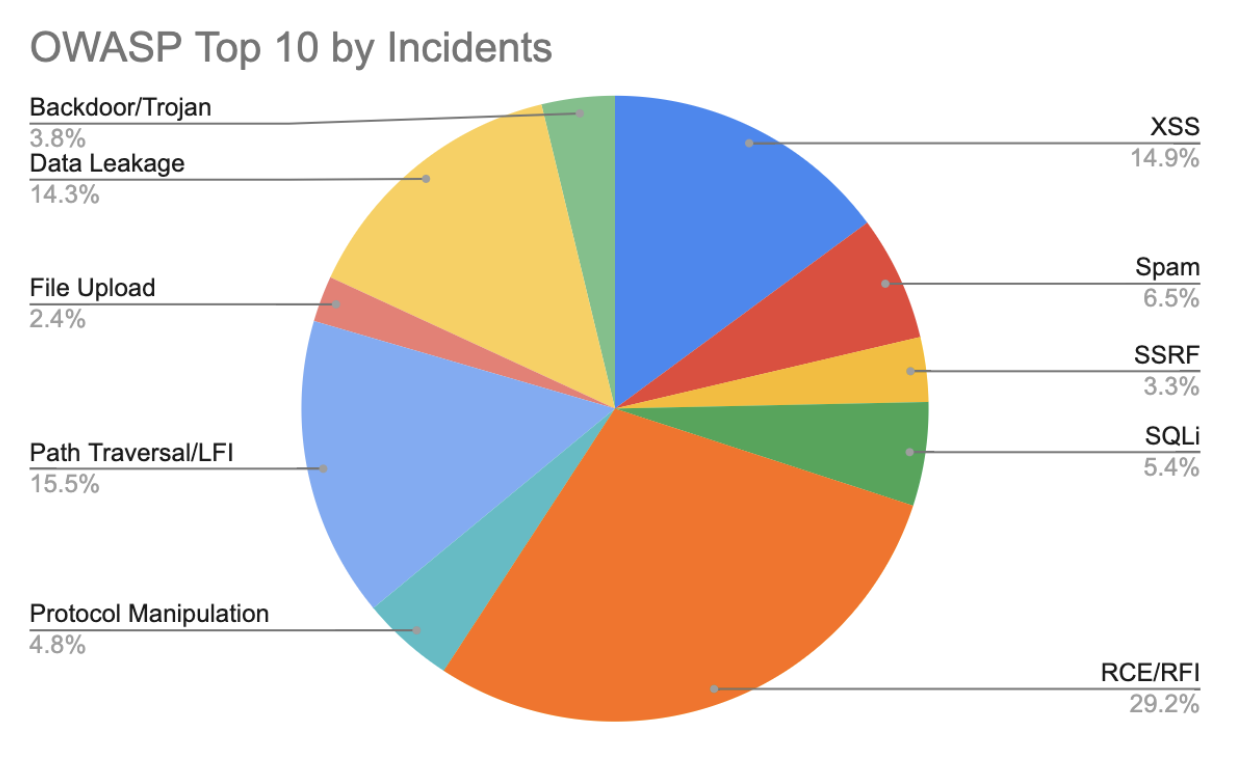
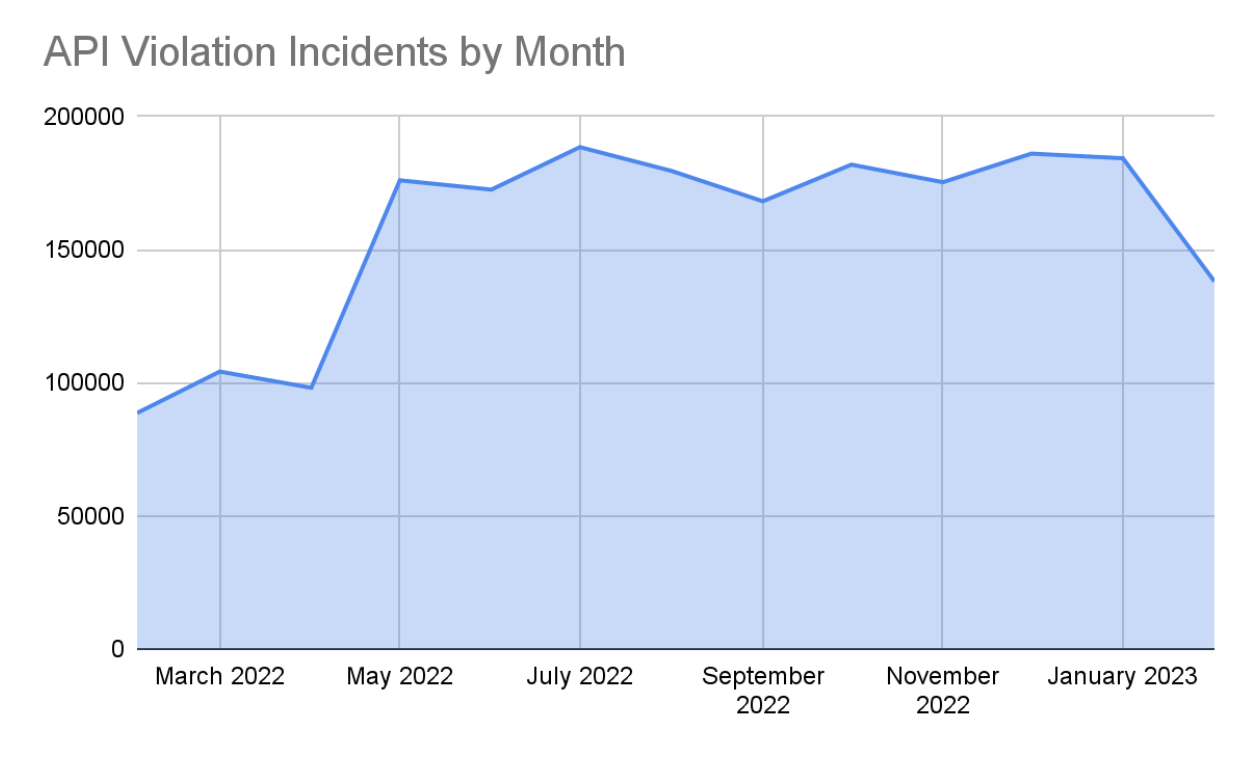
The most common attack we saw on APIs was, unsurprisingly, API violations, or calls that don’t align with the intended definition of the API. It’s important to note that attackers use a myriad of attacks when they target APIs. Hence, layered security is an important part of application security. Attackers can target a site with a common attack, such as a SQL injection, path traversal, or cross-site scripting, but they can also use an application’s design flaws to create new access vectors. When investigating attacks on healthcare sites’ APIs, we found that remote code execution (RCE) and path traversal were tied for the second-most API attacks.
From May to December 2021, API violation incidents – or aggregations of attacks coming from the same source using the same tool in the same time frame – remained relatively steady at about 175,000 incidents per month.
Shadow APIs, or APIs that are undocumented and not maintained by normal IT management and security processes, but not removed, also present a threat to many industries. In comparison to other industry categories, healthcare has a low volume of such incidents. In the first two months of 2023, shadow API traffic represented about 4% of all traffic across healthcare sites that Imperva protects.
Bad Bots
Data scraping, account takeover, and other forms of automated fraud driven by bad bots is common in the healthcare industry. In 2021, Imperva tracked bad bots targeting vaccine appointment sites in an effort to reserve appointments in bulk and resell them at higher prices.
Bots account for an average of 42% of traffic on healthcare sites, with bad bots making up a majority of that traffic (32%). “Good bots” can be helpful in some contexts. They can provide updated waiting times, track available appointments, and more. But, while good bots were created with helpful intentions in mind, they can be exploited by bad actors. Bad bots, on the other hand, are purposefully designed to carry out malicious attacks that make it harder for patients to access the services and care they need, and for healthcare sites to provide it.
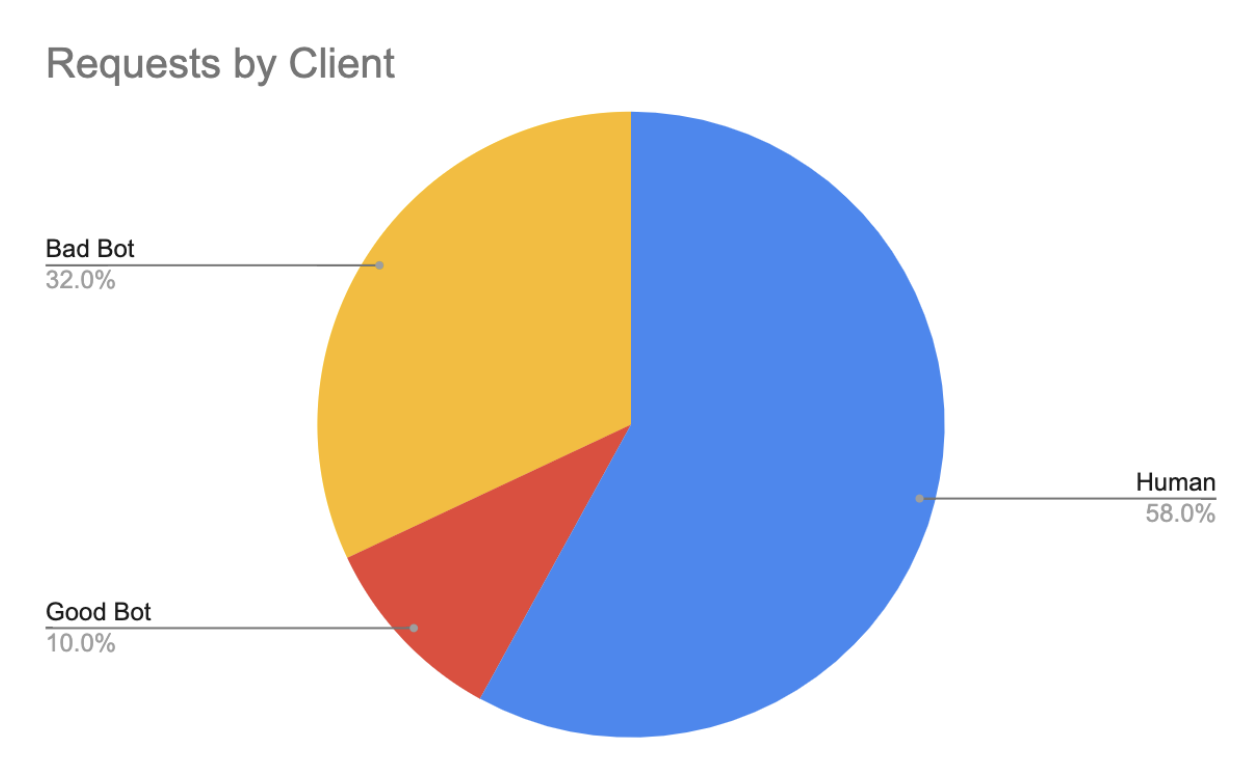
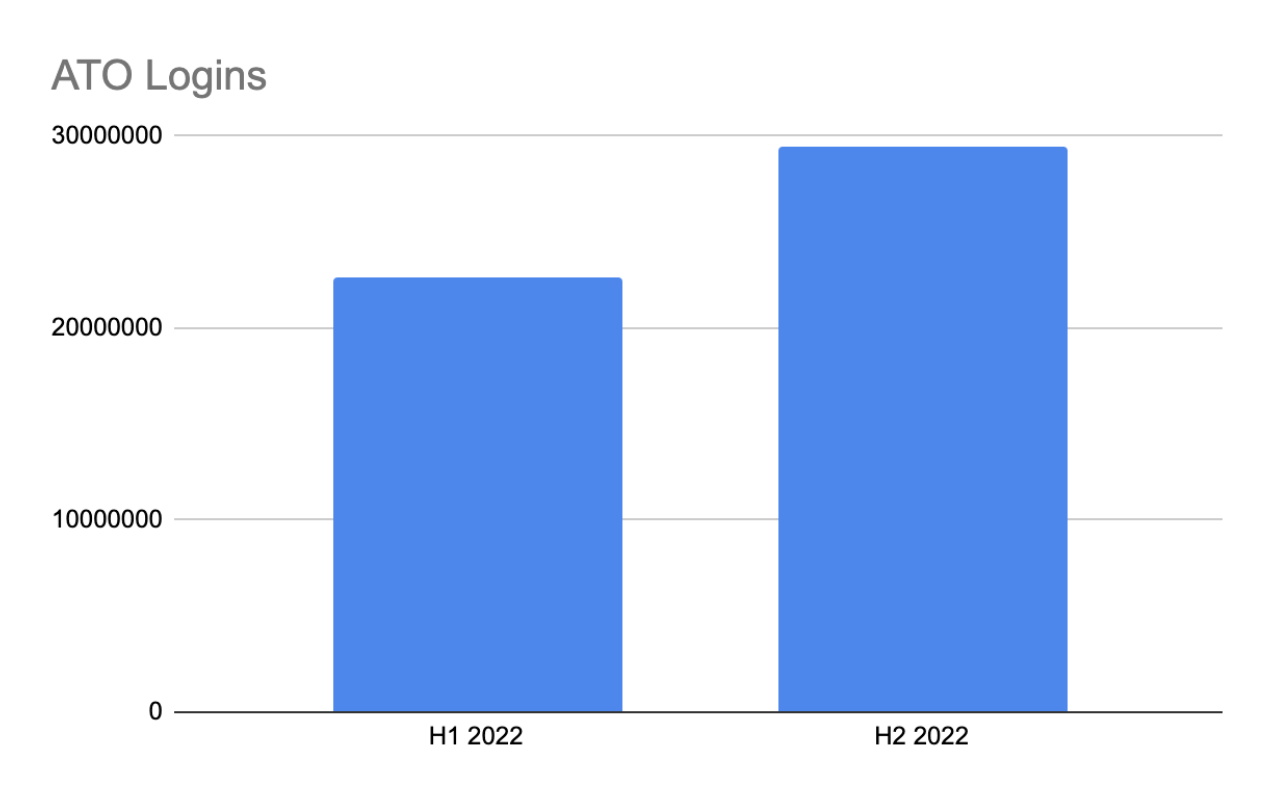
Account takeover (ATO) is another common automated attack in which bots gain access to accounts with the purpose of compromising valuable PHI, payment information, insurance details, and more. In the last month, ATO accounted for 30% of all advanced bot attacks.
ATO attacks grew from H1 to H2 2022 due to a targeted attack on a health provider.
Imperva provides protection and compliance for critical healthcare data and applications
Driving more effective patient outcomes starts with securing mission-critical apps and data. Given the value of PHI, the healthcare industry must take steps to stay ahead of motivated attackers, while providing continued care for those who need it most.
Imperva Application Security covers all EHR, EMR, and insurance systems – no matter where they are located. Imperva solutions prevent malicious activity anywhere; on-premises, in the cloud, spread across multiple clouds, or any combination thereof. Powered by machine learning algorithms, threats and anomalous behavior are detected in real-time.
Imperva Data Security Fabric was uniquely designed to integrate with leading electronic healthcare record systems, bringing complete visibility and security analytics to the “who, what, where, when, how, and should” questions of data activity. With support for EMR/EHR systems, Imperva closes risky gaps for healthcare organizations that, for many years, have had little or no security or compliance visibility into these critical systems.
Learn how Imperva products and solutions can protect the healthcare industry.
Try Imperva for Free
Protect your business for 30 days on Imperva.













