The NFL's San Francisco 49ers team is recovering from a cyberattack by the BlackByte ransomware gang who claims to have stolen data from the American football organization.
The 49ers confirmed the attack in a statement to BleepingComputer and said it caused a temporary disruption to portions of their IT network.
While the 49ers did not confirm whether hackers successfully deployed the ransomware, they said they are still in the process of recovering systems, indicating that devices were likely encrypted.
"The San Francisco 49ers recently became aware of a network security incident that resulted in temporary disruption to certain systems on our corporate IT network. Upon learning of the incident, we immediately initiated an investigation and took steps to contain the incident.
Third-party cybersecurity firms were engaged to assist, and law enforcement was notified.
While the investigation is ongoing, we believe the incident is limited to our corporate IT network; to date, we have no indication that this incident involves systems outside of our corporate network, such as those connected to Levi’s Stadium operations or ticket holders.
As the investigation continues, we are working diligently to restore involved systems as quickly and as safely as possible."
San Francisco 49ers
To conduct a ransomware attack, threat actors breach a corporate network and silently spread to other devices while stealing data. The hackers ultimately deploy malware that encrypts all of the devices on the network, while leaving ransom notes demanding a cryptocurrency payment to receive a decryptor.
The ransomware gangs then use the stolen files as leverage, threatening to release them if they are not paid a ransom.
The BlackByte gang claimed responsibility for the 49er's attack yesterday, right as the NFL gets ready for Super Bowl 2022, by beginning to leak files that they claim are stolen files.
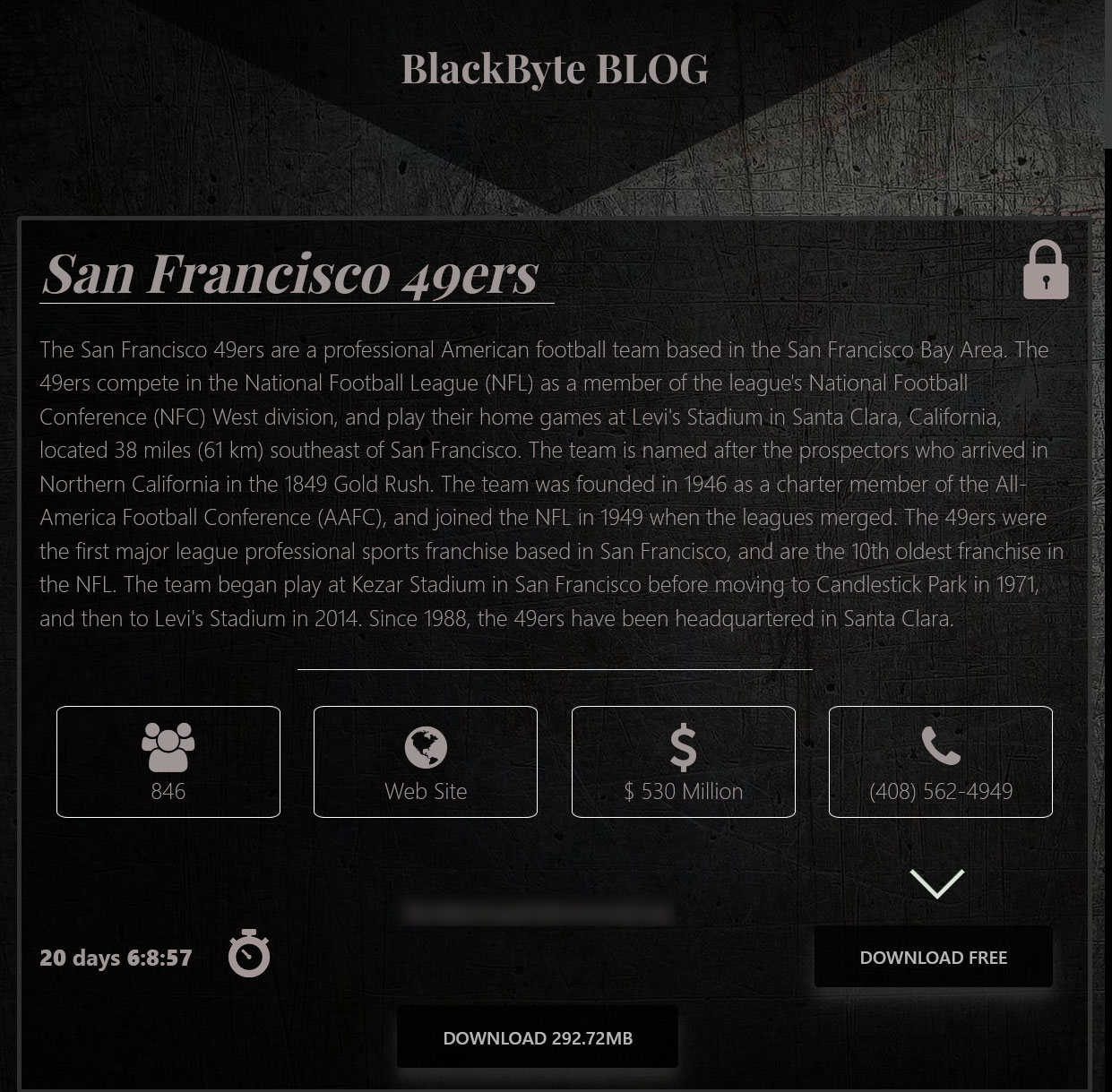
Source: BleepingComputer
The leaked data is a 292MB archive of files that the threat actors say are stolen 2020 invoices from the 49ers' network.
BlackByte usually releases its victims' data in increasing amounts to further pressure the victim into paying.
While it is not known how much data has been stolen during the attack on the 49ers, BlackByte has stolen gigabytes of data from previous victims.
Who is BlackByte?
The BlackByte ransomware operation launched in July 2021 when it began targeting corporate victims worldwide.
The ransomware gang is not particularly active compared to other groups, but they have conducted numerous successful attacks, meaning the enterprise should not ignore them.
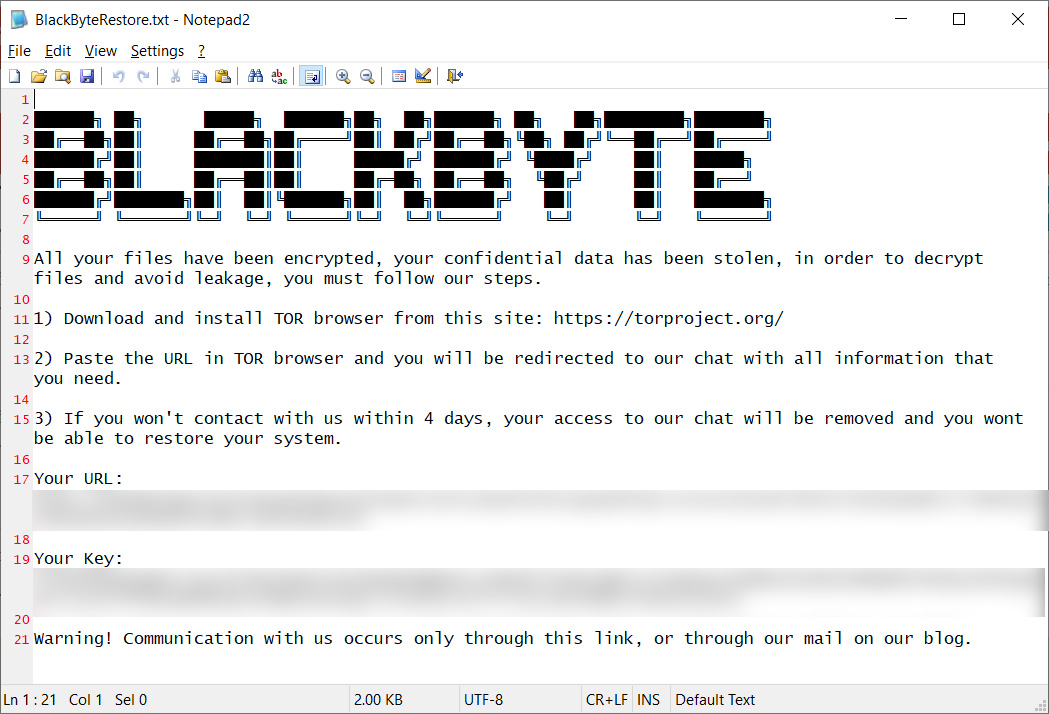
Source: BleepingComputer
The ransomware gang is known to utilize vulnerabilities to gain initial access to a corporate network, illustrating the need to always have the latest software updates installed.
In October 2021, the BlackByte operation made the significant mistake of reusing the same decryption/encryption key in multiple attacks.
While BlackByte quickly fixed the bug, it allowed cybersecurity firm Trustwave to create a free decryptor allowing some victims to recover their files for free.


.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now